Key Takeaways
- Cut alert noise and prioritize high-risk signals so your SOC catches real attacks faster than teams stuck clearing busywork.
- Create a repeatable incident-response workflow with clear owners, tested playbooks, and tight coordination with IT and cloud teams to speed up every decision.
- Protect analysts from burnout by reducing low-value alerts, improving context in investigations, and investing in training so the team can do steady, focused work.
- Turn threat intelligence into a daily filter that adds useful context and relevance, so you stop collecting feeds and start spotting what matters.
In the fight against cybercrime, Security Operations Centres (SOCs) are at the forefront.
They are responsible for finding threats, investigating suspicious activity, and responding to incidents before damage escalates. Still, many businesses face the same operational problems year after year, even though they spend more on tools, automation, and staff.
Alert backlogs grow. Analysts burn out. Incidents slip through unnoticed. Leadership questions the return on investment. These outcomes are not caused by a lack of effort or intent. They result from structural, operational SOC challenges that are often underestimated.
Understanding why SOCs struggle requires looking beyond technology. This blog discusses the most common problems SOCs face today, why they persist, and what practical steps can help overcome them.
Alert Overload and Signal Fatigue
One of the most visible SOC challenges is the sheer volume of alerts.
Modern security stacks get alerts from applications, identity systems, networks, cloud platforms , and endpoints. Even though visibility has improved, the signal quality often hasn’t.
Some common issues are:
- Thousands of alerts with little context
- Duplicate or low-value detections
- Poor prioritisation of critical events
- Analysts spending time closing noise
SOC challenges caused by alert fatigue make analysts less effective and more likely to miss threats.
Limited Visibility Across Environments
SOC visibility is often fragmented.
As companies adopt cloud, SaaS, and remote work models, security telemetry is distributed over multiple platforms. SOC teams frequently lack a unified view of activity.
Visibility-related SOC challenges include:
- Blind spots in cloud and identity layers
- Inconsistent logging across systems
- Delayed or incomplete telemetry
- Limited insight into lateral movement
Detection becomes reactive instead of proactive when there isn’t full visibility.
Tool Sprawl and Integration Complexity
Many SOCs accumulate tools over time without a clear integration strategy.
This means:
- Plenty of consoles and dashboards
- Manually correlating tools together
- Inconsistent detection logic
- Increased operational overhead
One of the most common problems in SOC is tool sprawl, which makes things more complicated without necessarily improving outcomes.
Shortage of Skilled Analysts
People remain the most critical component of a SOC.
However, many organisations struggle to recruit, train, and retain experienced analysts. The skills gap contributes directly to SOC challenges like slow investigation and irregular response.
Common workforce issues include:
- High analyst turnover
- Long onboarding times
- Overreliance on junior staff
- Limited opportunities for skill development
Even strong processes start failing when people are stretched too thin.
Ineffective Incident Response Workflows
Response is what stops attacks, not just detection.
During incident response, a lot of problems emerge with SOC, such as confusion and delays.
Typical response issues include:
- Unclear ownership during incidents
- Manual, error-prone response steps
- Lack of tested playbooks
- Poor coordination with IT and cloud teams
Without well-defined workflows, response speed and consistency suffer.
Inadequate Use of Threat Intelligence
Threat intelligence is often underutilised.
Many SOCs get threat feeds, but integrating intelligence into everyday work is still challenging.
Intelligence-related SOC problems include:
- Contextless indicators of compromise
- Lack of relevance to the organisation’s environment
- Difficulty operationalising intelligence
- Overwhelming volume of data
SOCs that work well focus on actionable intelligence instead of raw data.
Difficulty Measuring SOC Effectiveness
People often ask SOC leaders to demonstrate value, but it’s hard to come up with useful metrics.
Some common measurement-related SOC problems are:
- Overreliance on alert counts
- Lack of outcome-based metrics
- Difficulty linking SOC activity to risk reduction
- Limited executive-level reporting
Without the right metrics, it is difficult to justify investment or guide improvement.
Automation That Fails to Deliver Expected Value
People often think that automation can help with SOC challenges, but the results vary.
Poorly implemented automation can:
- Escalate noise instead of reducing it
- Break workflows during incidents
- Create blind trust in automated decisions
- Mask underlying process issues
Automation works best when paired with strong processes and human oversight.
Misalignment Between SOC And Business Priorities
SOC teams often operate disconnected from business context.
This means:
- Misprioritisation of incidents
- Excessive focus on technical severity
- Limited understanding of business impact
- Friction with other teams
To address long-term SOC problems, it’s important to ensure security operations align with business risk.
Why SOC Challenges Persist Despite Investment
Many businesses spend a lot of money on tools and services, but the results don’t change.
This happens because:
- Tools are added without process redesign
- People are expected to adapt without support
- Metrics focus on activity rather than impact
- Continuous improvement is deprioritised
SOC problems recur when fundamental issues are not fully addressed.
What Effective SOC Improvement Looks Like
Organisations that successfully reduce SOC challenges take a disciplined approach.
They usually do this:
- Reduce alert volume through tuning and validation
- Improve visibility across identity, cloud, and endpoints
- Standardise and test incident response playbooks
- Use automation selectively and strategically
- Measure success through detection and response outcomes
These steps change SOCs from reactive monitoring centres to proactive defence teams.
When Organisations Should Reassess Their SOC Strategy
It is time to rethink your SOC strategy when:
- Alerts consistently outpace analyst capacity
- Incidents are detected late
- Analysts experience frequent burnout
- Leadership questions SOC effectiveness
These signals indicate systemic issues with the SOC that need to be addressed.
Summary
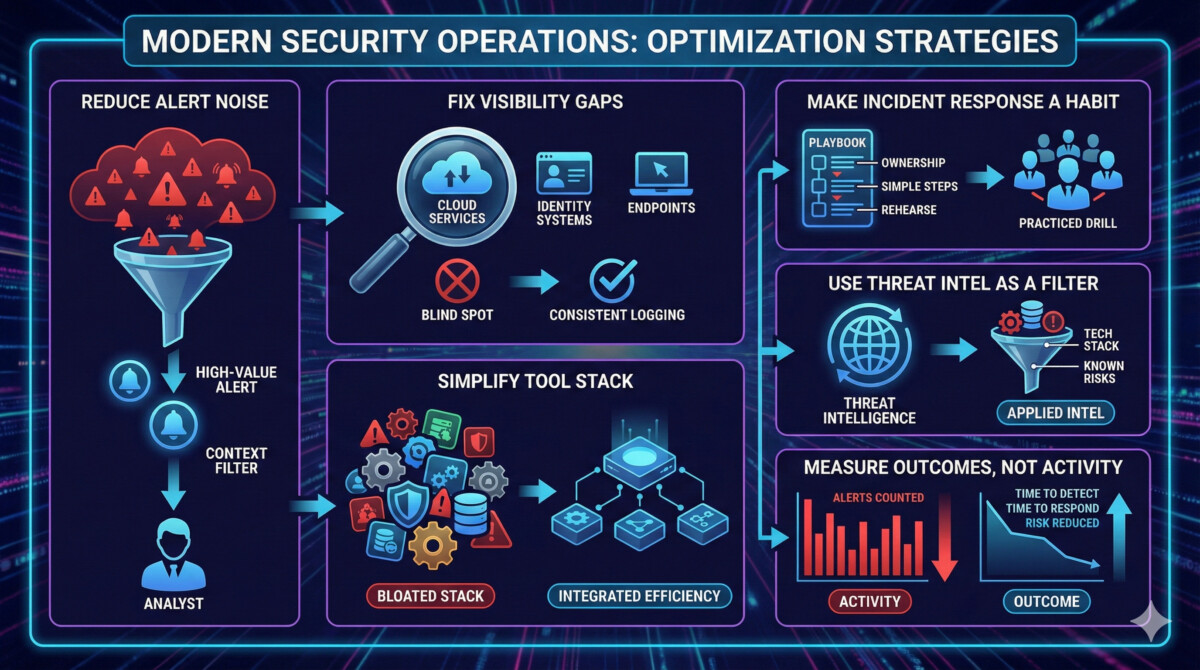
Running a Security Operations Center (SOC) is not failing because teams do not care or tools are missing. It fails because the work becomes unmanageable. The article breaks this down clearly: alert overload creates signal fatigue, visibility gets fragmented across cloud, SaaS, and remote devices, and tool sprawl forces analysts to jump between dashboards while real threats keep moving. Add a skills shortage and unclear incident response ownership, and you get the pattern most leaders recognize: growing backlogs, burnout, missed incidents, and tough questions about ROI.
For ecommerce founders and marketers, this matters because security issues quickly become business issues. A single incident can shut down storefronts, break customer trust, and pull teams off growth work for weeks. The fastest path to a stronger SOC is not “buy another tool.” It is tightening fundamentals:
- Reduce alert noise on purpose. Tune detections, remove duplicates, and require better context before an alert hits a human. When analysts spend their day closing low-value alerts, they miss the real ones.
- Fix visibility gaps before you chase advanced threats. Make sure logging is consistent across cloud services, identity systems, endpoints, and key apps. In many environments, even basic blind spots in identity and cloud activity are what make detection reactive.
- Simplify the tool stack and integration. Fewer tools that share data well beats more tools that do not connect. A bloated stack raises overhead and slows investigations.
- Make incident response a practiced habit. Define ownership, build simple playbooks, and rehearse them. Manual, unclear steps are where delays and mistakes happen.
- Use threat intelligence as a filter, not a firehose. Many teams collect feeds but cannot apply them. Focus on intelligence that matches your tech stack, your vendors, and your known risks.
- Measure outcomes, not activity. Counting alerts is easy, but it does not prove risk went down. Track time to detect, time to respond, and which fixes actually prevent repeat incidents.
If you operate in ecommerce, also remember that compliance pressure often increases the workload. Common audit and assurance pain points, like access control gaps, incomplete asset inventories, and vendor risk management, can create extra noise and urgency if they are not handled early. Treat those as SOC inputs, not last-minute paperwork.
Next Steps
A SOC gets stronger when you reduce noise, improve visibility, simplify tools, and run clear response playbooks that real people can follow under stress. If you implement only one change this week, start by cutting alert volume and adding better context, because that single move lowers burnout and improves detection at the same time. Next, pick one gap to close (cloud logs, identity visibility, or response ownership), set a 30-day target, and track improvement with simple outcome metrics. If you want to go further, audit your access controls, asset inventory, and key vendor risks, then align your SOC workflows to those realities so security supports growth instead of interrupting it.
Before trying to fix ongoing SOC problems, organisations should begin with an honest assessment of alert quality, visibility gaps and response workflows. In a lot of cases, simplifying instead of adding more tools is what leads to improvements.
CyberNX is a cybersecurity firm that provides AI-powered SOC services that are designed for modern security threats. They have a centralized, shared model that helps with 24/7 threat hunting. They make detection more accurate, response workflows more efficient, and align security operations with real-world threat behaviour.



